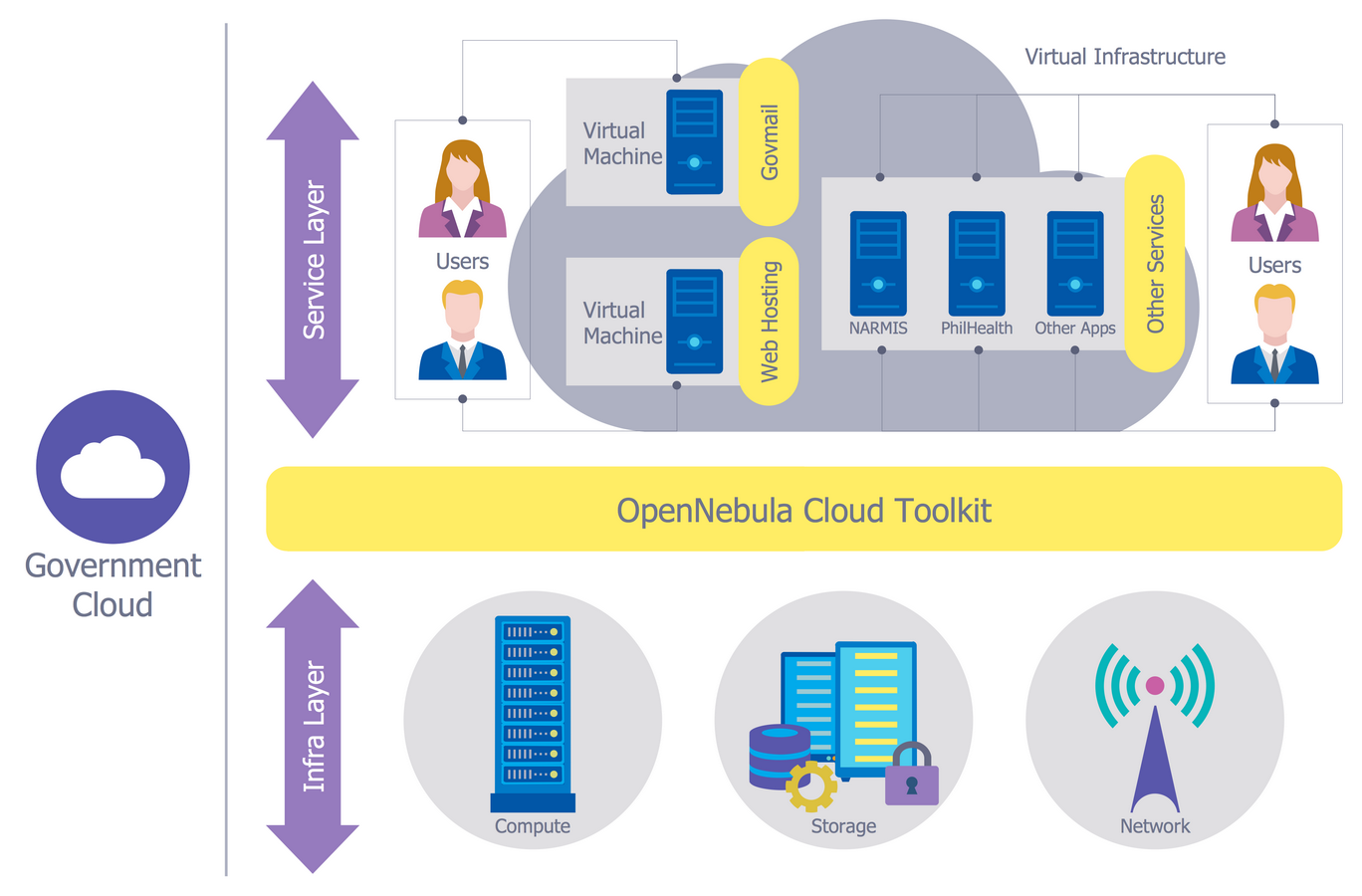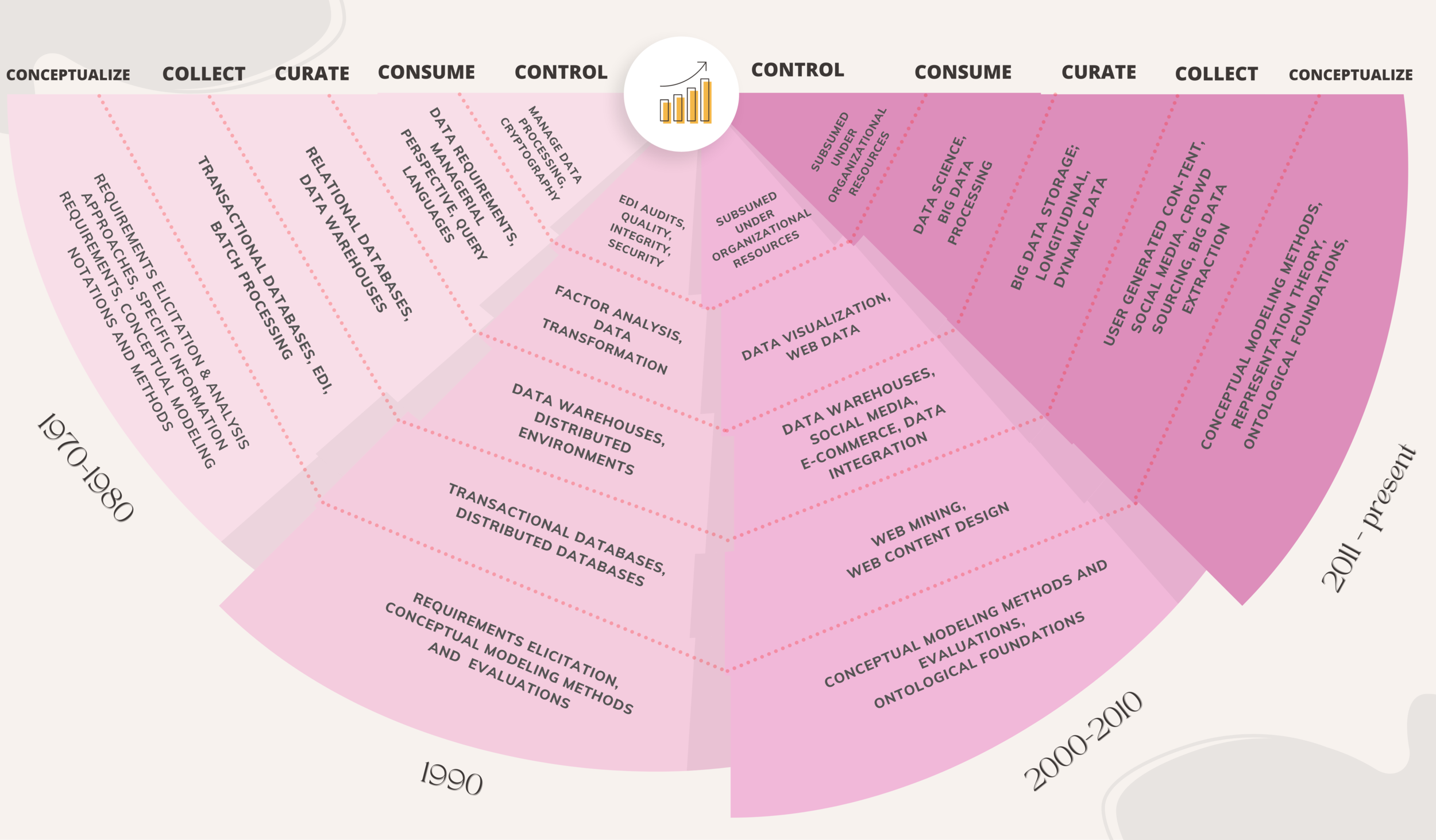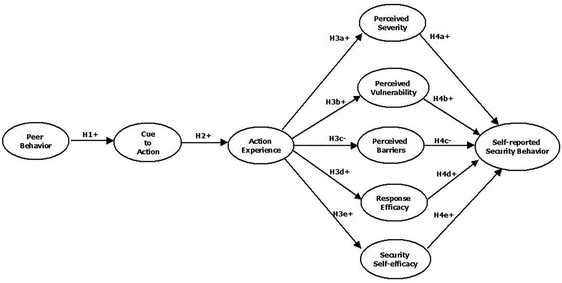
Sustainability | Free Full-Text | Epistemological and Bibliometric Analysis of Ethics and Shared Responsibility—Health Policy and IoT Systems
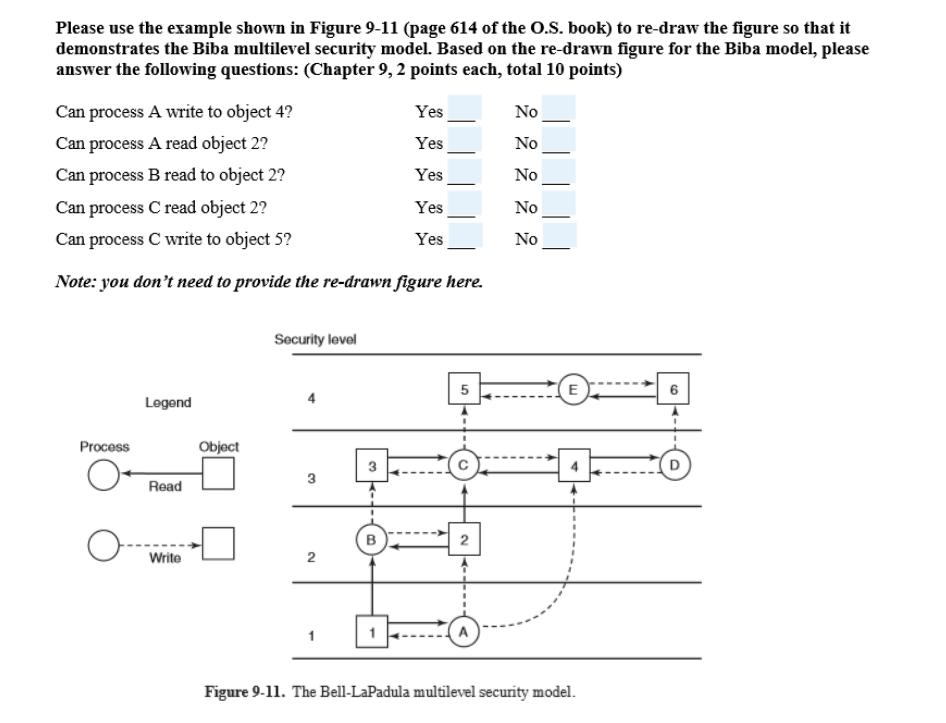
1] B. Genge, C. Siaterlis, and M. Hohenadel. AMICI: an assessment platform for multi-domain security experimentation on critica