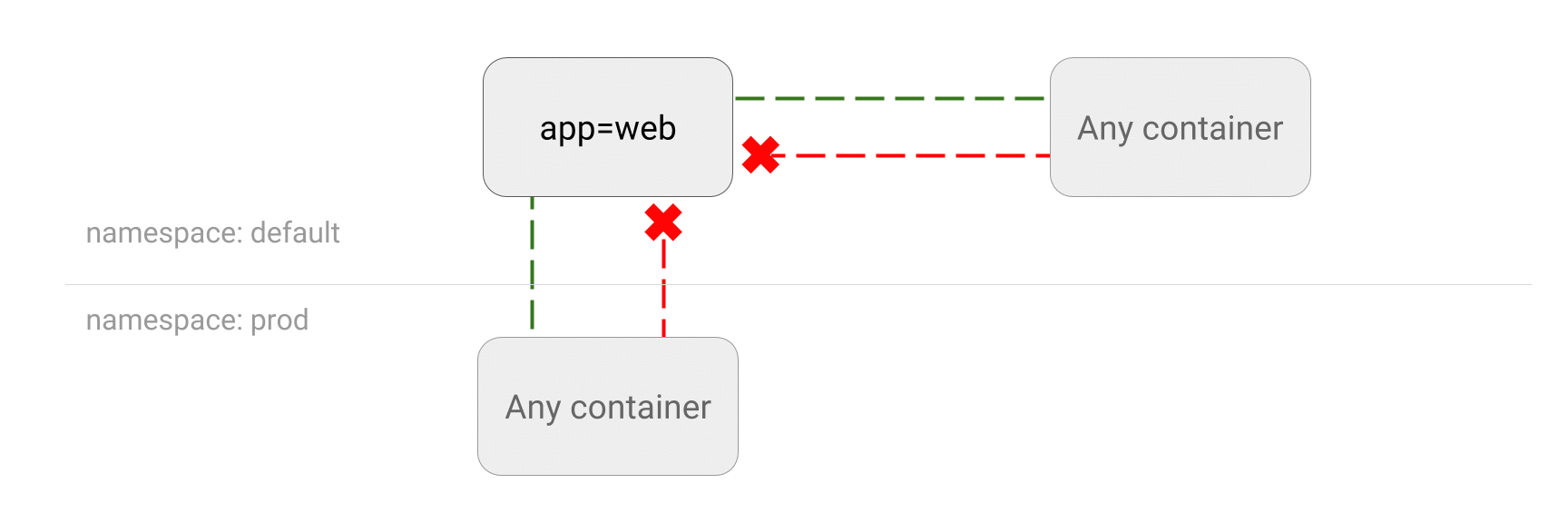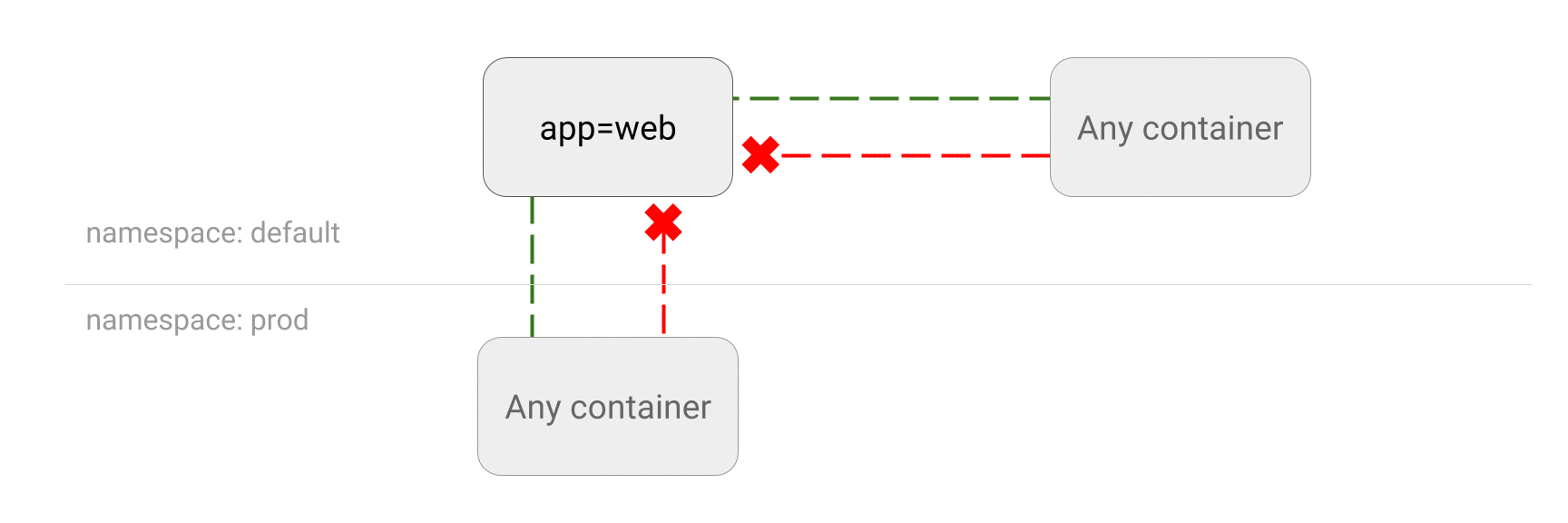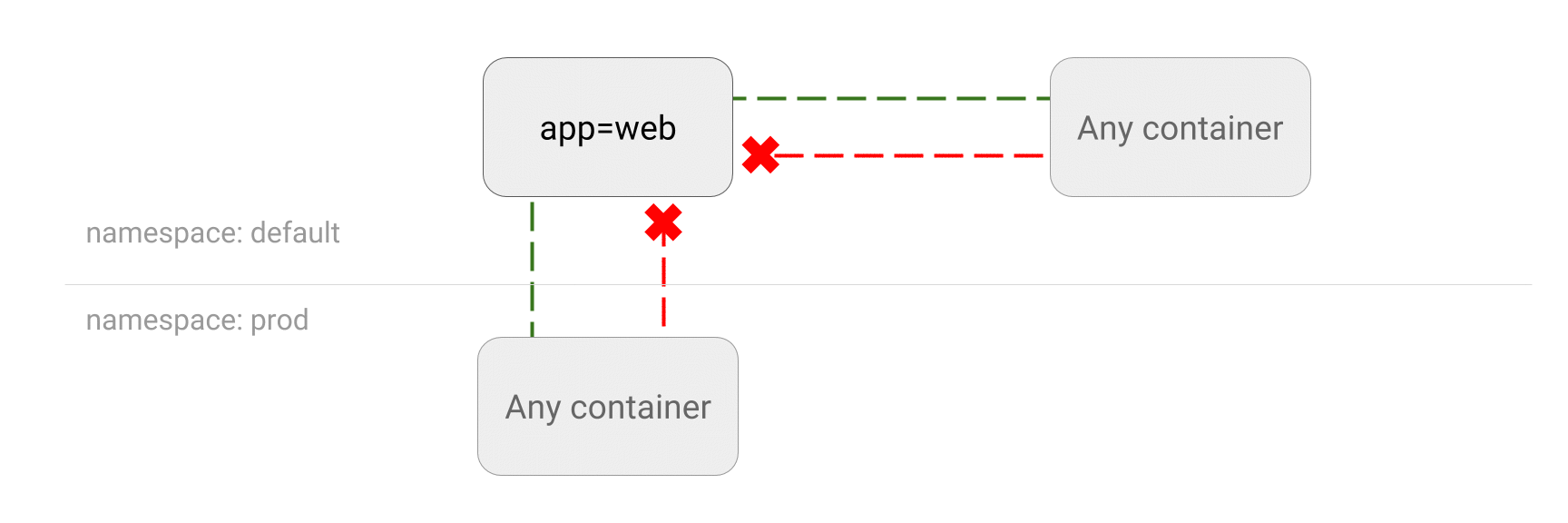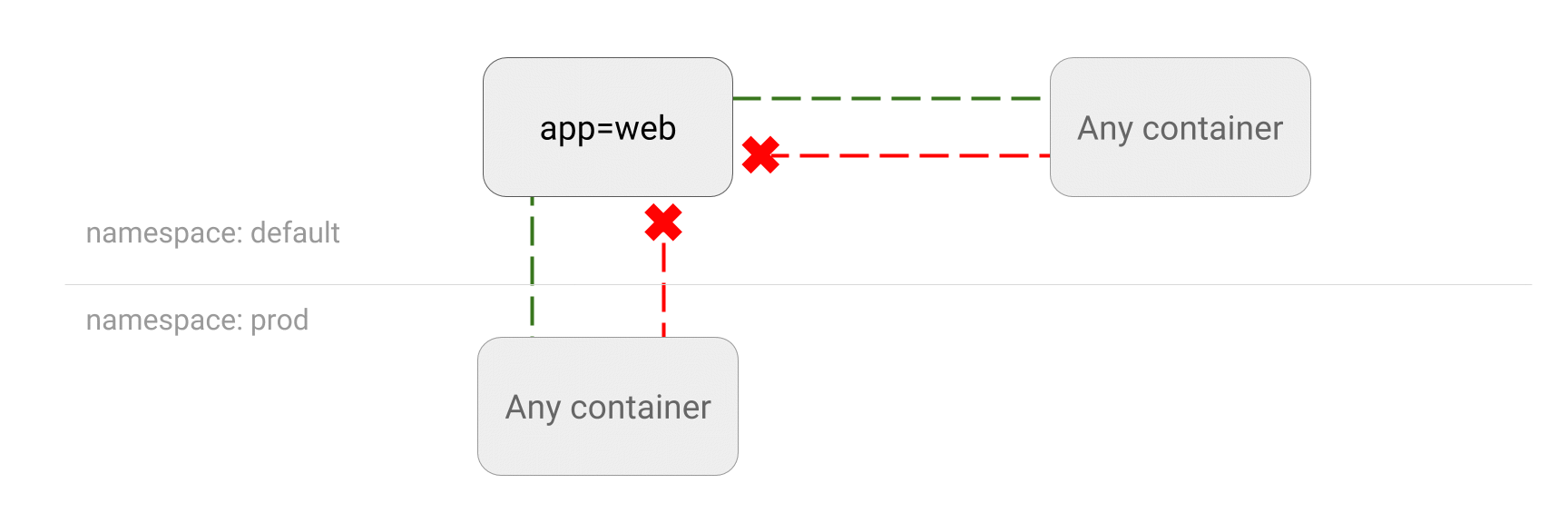
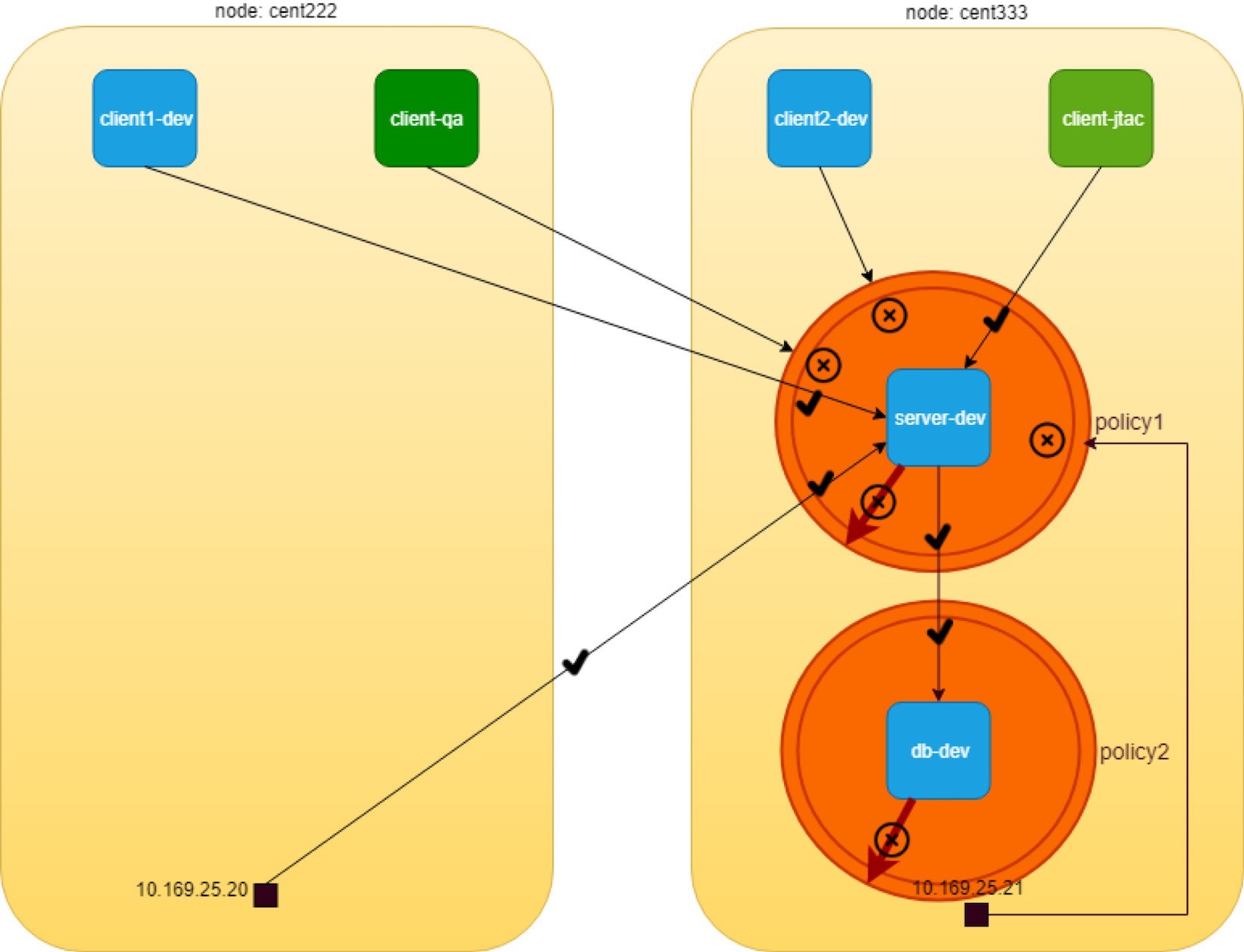
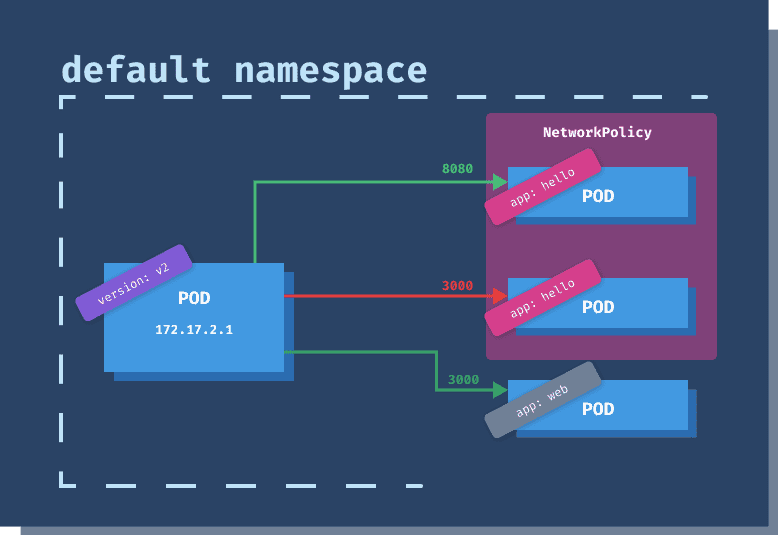
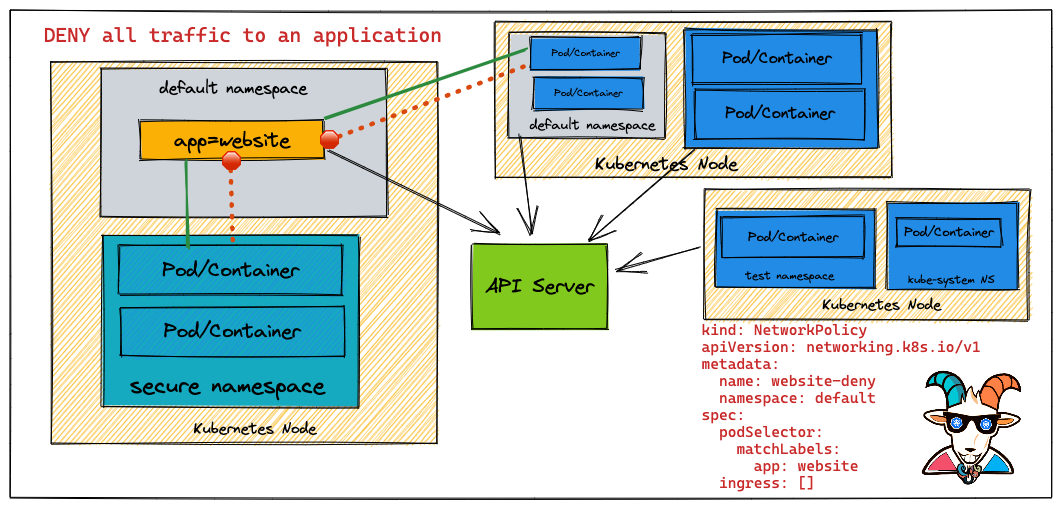
Generating Kubernetes Network Policies Automatically By Sniffing Network Traffic | by Murat Celep | ITNEXT
GitHub - ahmetb/kubernetes-network-policy-recipes: Example recipes for Kubernetes Network Policies that you can just copy paste
Lifecycle of Kubernetes Network Policies and Best Practices | by Murat Celep | May, 2021 | ITNEXT | ITNEXT